Latest Posts

Crafting Malicious Facebook Ads via Instant Experiences
Everyone who uses Facebook has seen them: slick, fast-loading ads that open up into a full-screen experience without ever leaving the app. These are...
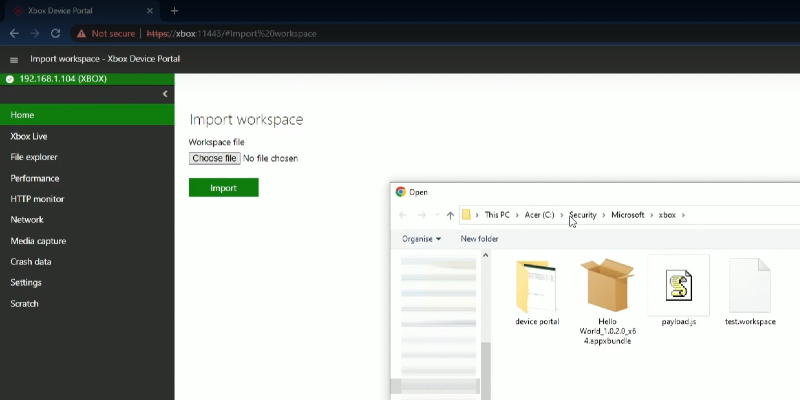
XSS to RCE - Xbox Device Portal
The Xbox Device Portal is an invaluable tool for developers, offering remote access to an Xbox console in developer mode via a web browser. It allows...

Bountycon 2022 - Android Trinity PWN
Whilst working on the BountyCon 2022 CTF, I spent the majority of the time focusing on the Android Trinity challenge. This was one of two PWN...

Disclosing BCC Recipients of an email
This post will cover an interesting logic flaw found in a private bug bounty program. Whilst the name of this company will be known as...

Abusing Facebooks Call To Action to launch internal deeplinks
Ever noticed that big blue button on the top of every Facebook page? This feature, known as Call to action or CTA is designed for user...

Open redirects are not dead! Or are they?
Over the last few years doing bug bounties, it's becoming more and more common for companies to reject reports about Open Redirects. Once upon a...